More and more file shared between forum users, and a question arise. "Is the file safe?", "Is it safe to open this file? My antivirus XXX detect the file as YYY"
A forum user might reply that it maybe a false-positive detected by antivirus (and then begin comparing which antivirus is better). or something like this "To be safe, run inside sandboxie or virtual machine."
So today's topic is - How safe is sandboxie?
To begin with, how about some introduction first.
How sandboxie work?
According to main page, it's pretty clear how sandboxie work. Looking at gif images will surely made you understand in less than a second.
Sandboxie runs your program INSIDE isolated space. For example, says a software... let's call it "destroy_my_pc.exe". This software will alter your window's registry, modify file data, delete file on your computer and add some files into your computer. When you run this software using sandboxie, All the changes made by "destroy_my_pc.exe" on your computer will stays inside the sandbox, inside the isolated space.
Sandboxie will create a virtual space for your program. The space is usually on C:\Sandbox (Unless you changed the setting). So let's say the program wanted to create some file on your computer. Let's say it want to create a file on "C:\autorun.bat". When the program is run through sandboxie, the file will physically created on "C:\Sandbox\User\DefaultBox\drive\c\autorun.bat", not on "C:\autorun.bat". The software doesn't know that it runs on isolated space. The programs will see that the file resides on C:\autorun.bat but actually the file is on "C:\Sandbox\User\DefaultBox\drive\c\autorun.bat".
Let's say the software doesn't want to create autorun.bat when it is already exists. What it do is it will check the folder/drive content one by one to see if the file exists. Firstly, it do this by requesting the windows "What 's on C:\ ?". The windows reply back by giving file entries, such as: "Boot", "Program Files", "Users", "Windows", "some", "etc", etc", "etc...", "pagefile.sys", "autorun.bat" (<- Hey look... It's already there! Don't create the file!). So how the autorun.bat shows up on C:\ when it is not physically there? The file is on "C:\Sandbox\User\DefaultBox\drive\c\autorun.bat" Remember?
When a program inside a sandboxie request something from windows, sandboxie sits somewhere between windows and the program. While it sits there, it interfere the request by combining the entries returned by system with sandbox path. When a file got deleted inside sandbox, sandboxie simply remove deleted file from the entry. This is how it works with registry too. Sandboxie simply combine the two (real system and sandbox) into one and give it back to the program. How about altering file content? Simply by copying the file from physical path into sandbox path and alter the file data inside the sandbox path.
EDIT: Here I found something more to help you understand. The use of paper metaphor is most correct and easily understand. Source: WhatIsSandboxie?
EDIT: Here I found something more to help you understand. The use of paper metaphor is most correct and easily understand. Source: WhatIsSandboxie?
Think of your PC as a piece of paper. Every program you run writes on the paper. When you run your browser, it writes on the paper about every site you visited. And any malware you come across will usually try to write itself into the paper.Traditional privacy and anti-malware software try to locate and erase any writings they think you wouldn't want on the paper. Most of the times they get it right. But first the makers of these solutions must teach the solution what to look for on the paper, and also how to erase it safely.On the other hand, the Sandboxie sandbox works like a transparency layer placed over the paper. Programs write on the transparency layer and to them it looks like the real paper. When you delete the sandbox, it's like removing the transparency layer, the unchanged, real paper is revealed.
How safe it is?
Sandboxie is pretty safe if you are using it right. Let's say you run a browser inside the sandboxie, downloaded some program which turned out to be a virus, and run it inside sandbox. The virus changed everything and deleted everything to make the windows unbootable. It also tried to copy files to external drive. But what really happen is all changes is inside the sandbox. When you restart your computer, your windows will still remain intact like nothing happens. What really infected is your sandbox. In fact, you can delete all your sandbox content by right-clicking it. Yes sandboxie is pretty safe.
When does it not safe?
As explained before, sandboxie combine the system file and registry with sandbox file and registry. A program running on sandbox can see and read the system, but cannot write to it - all write goes into sandbox and subsequent read/write will be performed inside the sandbox.Sandboxie will not create a new fresh windows environment but rather a copy of your system. Well not exactly a full copy, but only copy when it is necessary such as when a program running inside sandbox wanted to write to an existing file, sandboxie will copy the file into sandbox first and then redirect the write into sandbox and all subsequent read and write will be on sandbox path.
Let's say you downloaded a file named "openme.exe" and begin suspicious with the file as your antivirus detect the file as trojan or dangerous malware. But you are not convinced. You turned off the antivirus and run the file inside the sandboxie. Then, you monitored the process and suddenly the process terminated. You inspected your sandbox content to see what changes made by the program - nothing can be found. So you delete the file as it does nothing. Suddenly, the next when you tried to login into your gmail account or facebook account or yahoo account, you can't. Your password has been changed by someone. All your account has been hacked. You decided to update your antivirus program and definition and scan the entire system, but the result is everything clean. Nothing infected your system. So what happened exactly?
What really happen is the program is instructed to collect all sensitive data on the victim computer. When you execute the file "openme.exe", the program will read your sensitive data, bypass firewall maybe and transmit all sensitive data to the attacker.
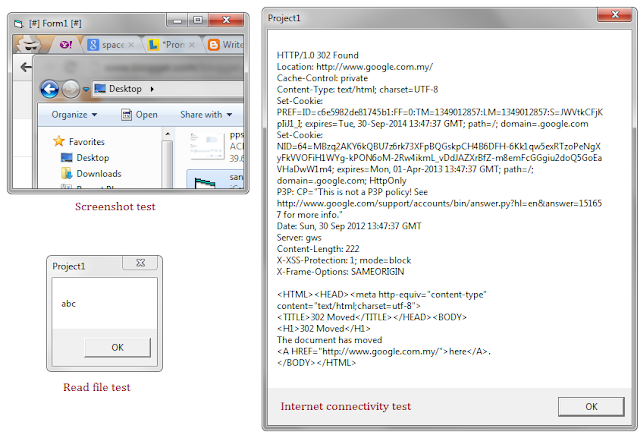
To prove this, I made a quick simple test program using VB6.0 and run inside sandboxie using its default settings. The program will run this test:
- Internet connectivity test.
- File read test
- Screenshot test
All test run successfully.
All test run successfully.
How to be safe?
Stay away from suspicious file or web page, never open them. If you still wanted to open it, use a completely isolated environment such as virtual machine and perhaps with network function disabled. If you want to use sandboxie to test suspicious file, block access to sensitive file, folder or registry by opening sandbox settings. Also, read the Sandboxie FAQ to understand how sandboxie works, how can it protect your system and what it cannot protect. Don't forget to use antivirus and firewall.
I've been using sandboxie nearly about 3 years. As a sandboxie user I love the features and how it works. I used sandboxie primarily to isolate games and some programs from my computer. Whenever I need to format my computer, I just restore my sandboxie.ini to the windows folder without need to reinstall all games. So far, I encounter zero problems by doing this. Even online games with cheat protection engine does work.







Bro... lu pakai version berapa?
ReplyDeleteAda serial key tak????, meh kongsi sikit...
Sent to puercoswar[at]gmail[dot]com
Time kacih....
3.74 ;)
Delete>>>>> Download Now
Delete>>>>> Download Full
>>>>> Download LINK
>>>>> Download Now
>>>>> Download Full
>>>>> Download LINK uM
5.16 wait for 5.17
ReplyDeleteI've been using AVG Anti virus for a number of years, and I'd recommend this product to all you.
ReplyDeleteROBLOX is driven by an ever growing community of over 300,000 creator players who generate an infinite variety of highly immersive experiences.
ReplyDeleteThese experiences range from 3D games and contests, to interactive adventures where friends can take on new identities exploring what it feels to be a dinosaur, a miner working a mine or an astronaut out in space.
Betting is easy with the internet.
ReplyDeleteรอยัล1688Online gambling games are open to the players to gamble indefinitely. The online casino of the site that makes the player happy with the risk of multiple online casinos. With easy access to online casino games through internet gambling. There are several ways to get players to gamble with us. The risk of online horoscope has increased. Today's online games can meet the needs of the player. Because there are types of online gambling games that are easy to understand, and online games to win more than 100 games to enjoy a full size because you do not have to travel to the casino. Because they can use online services and can earn money from the real risk. Not only this, the online game also broadcast live betting, so it is like betting from a real place. If you are one of the gamblers who want to gamble, the next step is to go online. And can meet all needs. Online Gambling Betting is the Way to Choose Who I came to the risk. Have you ever been here today? viva3388
Royal1688 Open up new channels of entry into the standard gambling and in the present day, the service of this online casino is also attractive to many gamblers enough to bet. Get well with getting into all kinds of gambling bets that are present to the player to respond to many gamblers and to subscribe to the casino. This line is also considered to be an area of free service for all gamblers who want to create a new experience with the best bets and also to give players a chance to bet. Casino games with betting guidelines and various types of gambling techniques allow gamblers to bet on fun games that we can make the original bet. No matter what kind of bets we make, we are delighted that the player succeeds in placing a very impressive bet on the secure and secure service channel. Make a bet with the casino online casino. Royal1688
ReplyDeleteGoldclub Slot Current Betting Sites To risk the world wide. The gambling industry. Global Betting Options Online casino games are a fun activity that creates fun on a regular basis. The new wish to win the chance to create a good view. The opportunity to create a great financial. Meet the gamblers to the new way. The way to the game that led to the victory overwhelming. Meet the perfect betting game. Open the path of fun. Online casino games, casinos, slots, slots and many other leading sports are one of the online gambling sites that open the path to happiness. With many casinos are known to be excellent. Relaxing game, open the path of finance that perfect. A fun way to create gambling opportunities. Open your eyes to the gambling industry. Enjoy the fun. With more than 200 games to choose from more fun games, there are a lot of bonus money to give you a simple play. Bet on the web. คาสิโนออนไลน์
ReplyDeleteWow, absolutely fantastic blog. I am very glad to have such useful information.
ReplyDeleteดูหนัง
This post is useful to those who have read. I would like to share this post. To be more useful. คาสิโนออนไลน์
ReplyDeleteFor me this blog is great, this blog is moving very important issues.
ReplyDeleteThis comment has been removed by the author.
ReplyDeleteสมัคร slotxo คาสิโนออนไลน์ พนันกีฬาออนไลน์ สล็อตออนไลน์ เราคือตัวแทงตรงจากทาง slotxo และนอกจากบริการ แล้วเรายังมีเกมส์คาสิโนออนไลน์ชั่นนำที่เราได้คัดสรรให้คุณร่วมสนุก นอกจากนี้เรายังมี ทางเข้า slotxo ไว้ให้บริการ เล่นง่าย ให้ราคาดี บริการด้วยความประทับใจรวดเร็ว สะดวก และไม่จำกัดรอบการถอน พร้อมรับโปรโมชั่นพิเศษสุดจากเราอีกมากมาย
ReplyDeleteThanks for sharing this amazing post plz visit Sandboxie 5.41.0 Crack
ReplyDeleteYour Article Is Very Great And Useful Thanks For Sandboxie
ReplyDeleteSo nice I am enjoying for that post as for u latest version of this Security tool Available
ReplyDeletesandboxie crack
The content of your blog is exactly what I need, I like your blog
ReplyDeleteI sincerely hope your blog has a rapid increase in traffic density.
wordpress
blogspot
youtube
មាន់ជល់
Pretty great post. I simply stumbled upon your blog and wanted to mention that I have really loved surfing around your blog posts. Great set of tips from the master himself. Excellent ideas. Thanks for Awesome tips Keep it up
ReplyDeleteVideopad Video Editor Crack
REAPER Crack
Sandboxie Crack
HD Video Converter Factory Pro Crack
cracksite.net
The content of your blog is exactly what I needed, I like your blog,
ReplyDeleteI sincerely hope that your blog a rapid increase in traffic density,
which help promote your blog and we hope that your blog is being updated.
wordpress
blogspot
youtube
ហ្គេមស្លត់
i read a lot of stuff and i found that the way of writing to clarifying that exactly want to say was very good so i am impressed and i like to come again in future.
ReplyDeletewordpress
blogspot
youtube
កាស៊ីណូ
>>>>> Download Now
ReplyDelete>>>>> Download Full
>>>>> Download LINK
>>>>> Download Now
>>>>> Download Full
>>>>> Download LINK Bp